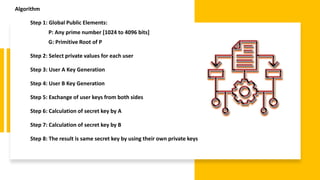
15+ Diffie Hellman Calculator
Quantum computing is a type of computation whose operations can harness the phenomena of quantum mechanics such as superposition interference and entanglementDevices that perform quantum computations are known as quantum computers. Specifically it takes quantum gates of.
Github Descent098 Diffie Hellman A Very Simple Implementation And Explanation Of The Diffe Helmen Key Exchange
Client Server Program in Java.

. They need to exchange some information over an unsecure communications channel to perform the calculation but an eavesdropper cannot determine the shared secret key based upon this information. The first 15 terms of Pell series are. You can now edit your.
John Gilmore Cracking DES. The Diffie-Hellman Key Agreement Protocol allows remote attackers from the client side to send arbitrary numbers that are actually not public keys and trigger expensive server-side DHE modular-exponentiation calculations aka a DHEater attack. There were other computers that had these features but the ENIAC had all of them in one package.
Instead of its decimal form 075 when you use the mod function in a calculator the remainder is a whole number. Make a note of the KeySpec value. Though current quantum computers are too small to outperform usual classical computers for practical applications larger.
Two popular algorithms that are used to ensure that data is not intercepted and modified data integrity are MD5 and SHA. You would need a calculator that is programmed to deal with 2048-bit numbers 617 digits long I think. Network Security - Part 6 Diffie-Hellman Key-Exchange 3329 Preview.
Ssh-keygen -b 4096 The -b flag instructs ssh-keygen to increase the number of bits used to generate the key pair and is suggested for additional security. Modular exponentiation is the remainder when an integer b the base is raised to the power e the exponent and divided by a positive integer m. AES is an encryption protocol and provides data confidentiality.
The calculator notation is in fact mod11 10 for TI-89 or 11 10 for CCJavaetc but that is just by notation of an operator from a comp. The Diffie-Hellman key exchange was designed on the basis of the discrete logarithm problem being difficult to solve. 15 mod 4 3.
Fundamental contributions to modern cryptography. Secrets of Encryption Research Wiretap Politics and Chip Design 1998 OReilly ISBN 1-56592-520-3. Make sure that Scientific is.
The Computer History Museum claims to house the largest and most significant collection of computing artifacts in the world. Cache Memory - Memory Address Structure Direct Mapping Part 2 3105 Preview. Generating publicprivate rsa key pair.
Witfield Diffie Martin Hellman Exhaustive Cryptanalysis of the NBS Data Encryption Standard IEEE Computer 106 tháng 6 năm 1977 pp7484. On a quantum computer to factor an integer Shors algorithm runs in polynomial time meaning the time taken is polynomial in the size of the integer given as input. Network Security - Part 7 RSA.
Keep in mind that the reason for doing modulus in the first place again is for staying inside of the field. In the code the iteration of the Java for-loop depends on the value of the variable noOfTerms. Version 220 2022-03-04 New feature.
IIS supports HTTP HTTP2 HTTPS FTP FTPS SMTP and NNTPIt has been an integral part of the Windows NT family since Windows NT 40 though it may be absent from some editions eg. It was Turing-complete and able to solve a large class of numerical problems through reprogramming. Open the Microsoft Windows Calculator.
Electronic Numerical Integrator and Computer was the first programmable electronic general-purpose digital computer completed in 1945. Did you ever wonder how two parties can negotiate a. DH Diffie-Hellman is an algorithm that is used for key exchange.
Diffie and Hellmans groundbreaking 1976 paper New Directions in Cryptography introduced the ideas of public-key cryptography and digital signatures the foundation of security protocols used on the Internet today. Shors algorithm is a quantum computer algorithm for finding the prime factors of an integer. These numbers are so large that most people never need to deal with them so most.
ENIAC ˈ ɛ n i æ k. 0 1 2 5 12 29 70 169 408 985 2378 5741 13860 33461 80782. When you divide 15 by 4 theres a remainder.
Point of view not modular arithmetic from a mathematical point of view. You can apply some specific settings to multiple sessions by right-clicking on a session copying its settings and pasting them to a group of sessions. It was developed in 1994 by the American mathematician Peter Shor.
The Finite Field Diffie-Hellman algorithm has roughly the same key strength as RSA for the same key sizes. Search for 252915 in Notepad to find the Key Usage attribute as. Pascal Junod On the Complexity of Matsuis Attack.
Calculator Tutorials - Casio fx-115ES 937 Start Mathematics. The client is a computernode that request for the service and the server is a computer node that response to the client. Certutil -user -CSP Microsoft Enhanced DSS and Diffie-Hellman Cryptographic Provider -repairstore My.
When the value of the loop variable i is 0 we display the first term of the Pell. Heres how to calculate it manually. Enter file in which to save the key.
1968 Dijkstra Edsger W. This includes many rare or one-of-a-kind objects such as a Cray-1 supercomputer as well as a Cray-2 Cray-3 the Utah teapot the 1969 Neiman Marcus Kitchen Computer an Apple I and an example of the first generation of Googles racks of custom. 15 4 375.
The client and server are the two main components of socket programming. Thus a 2048-bit Diffie-Hellman key has about the same strength. If you understand.
RSA is an algorithm that is used for authentication. Internet Information Services IIS formerly Internet Information Server is an extensible web server software created by Microsoft for use with the Windows NT family. Diffie-Hellman allows two parties the ubiquitous Alice and Bob to generate a secret key.
Modular exponentiation is exponentiation performed over a modulusIt is useful in computer science especially in the field of public-key cryptography where it is used in both Diffie-Hellman Key Exchange and RSA publicprivate keys. En1115 and computes the ciphertext C with. Cache Memory - Fully Associative Mapping N.
In our case the loop is iterating 15 times 0 to 14. For example youre calculating 15 mod 4. Browse our listings to find jobs in Germany for expats including jobs for English speakers or those in your native language.
Cache Level 1 2 3 Part 1 2715 Start. The work factor for breaking Diffie-Hellman is based on the discrete logarithm problem which is related to the integer factorization problem on which RSAs strength is based. The KeySpec is represented as a hexadecimal value.
A 5 A g a mod p 10 5 mod 541 456 b 7 B g b mod p 10 7 mod 541 156 Alice and Bob exchange A and B in view of Carl key a B a mod p 156 5 mod 541 193 key b A B mod p 456 7 mod 541 193 Hi all the point of this game is to meet new people and to learn about the Diffie-Hellman key exchange. 15 mod 4 15. Client Server Program in Java.
For this example 15 4 remainder 3 which is also 15 4 3 3. Mathematics is a valuable stepping stone to many careers including computing consulting data science education finance security and many moreBoise State offers Bachelor of Science degrees in Math optional Secondary Education emphasis and Applied Math optional Statistics emphasis plus minors in Math Applied Math and Math Teaching. Press Enter to use the default names id_rsa and id_rsapub in the homeyour_usernamessh directory before entering your passphrase.
The client needs very little CPU resources and network bandwidth. În matematică logaritmul este operația inversă a ridicării la putereAceasta înseamnă că logaritmul unui număr este exponentul la care un alt număr fix baza d trebuie să fie ridicat pentru a produce acel număr. In this video learn from.
You can now define your own default presets for sessions by right-clicking on a session and choosing Save session settings as default presets. În cazul cel mai simplu al exponentului natural logaritmul exprimă numărul de factori din înmulțirile repetateDe exemplu logaritm în bază 10 din 1000 este.
Diffie Hellman Key Exchange

Diffie Hellman Key Exchange For Authentication Download Scientific Diagram
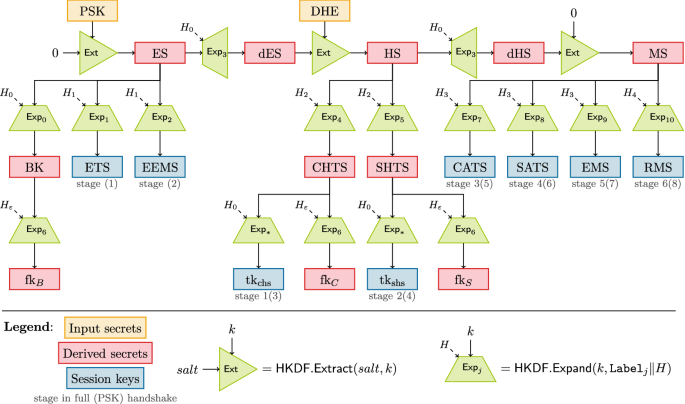
A Cryptographic Analysis Of The Tls 1 3 Handshake Protocol Springerlink
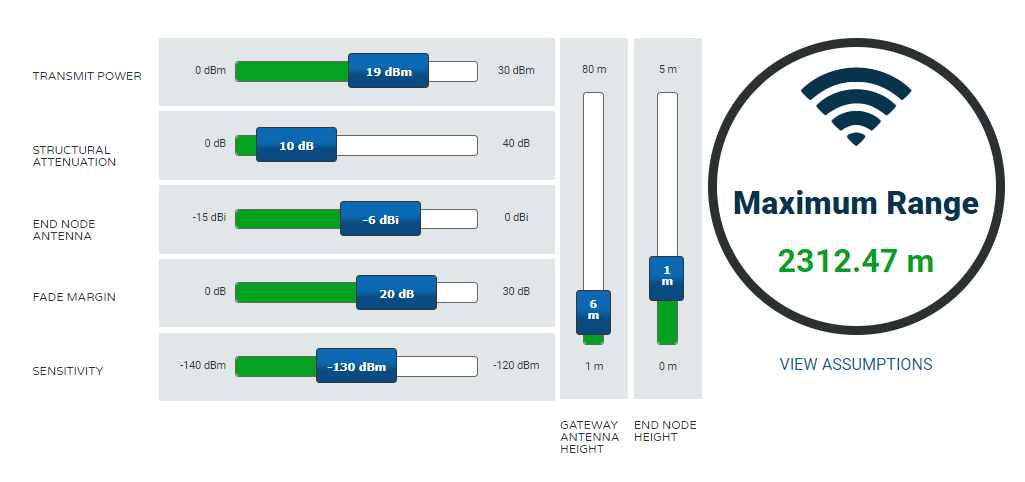
Symphony Link Internet Of Things Wireless Lpwa
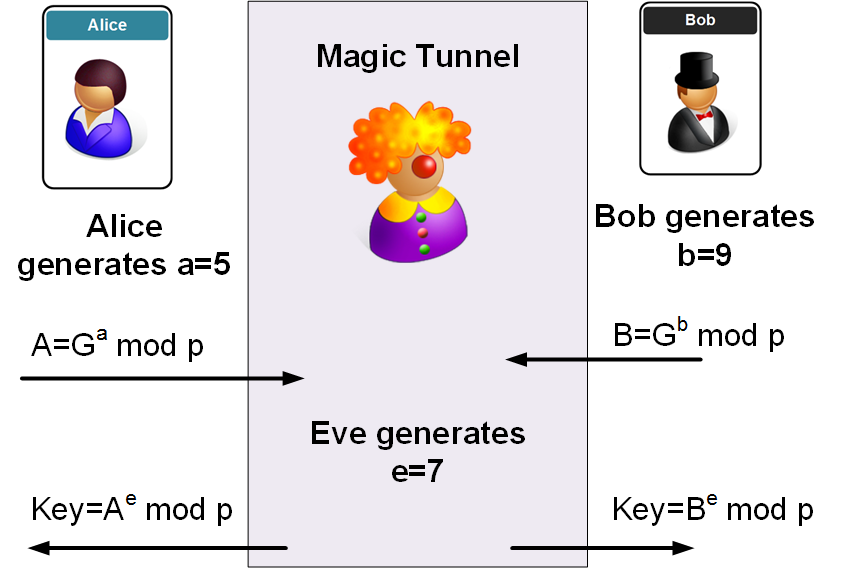
Diffie Hellman Man In The Middle

Solved 1 Explain The Diffie Hellman Key Exchange Algorithm Chegg Com
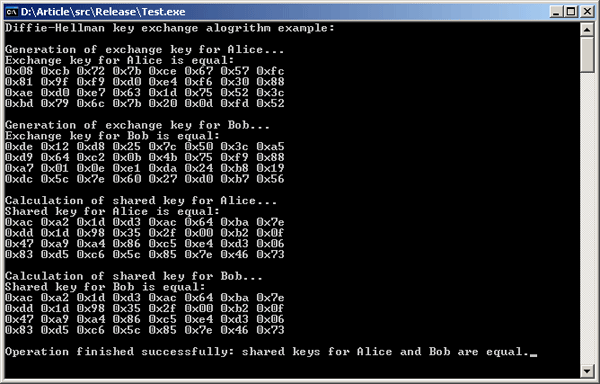
Implementation Of Diffie Hellman Algorithm Of Key Exchange Apriorit
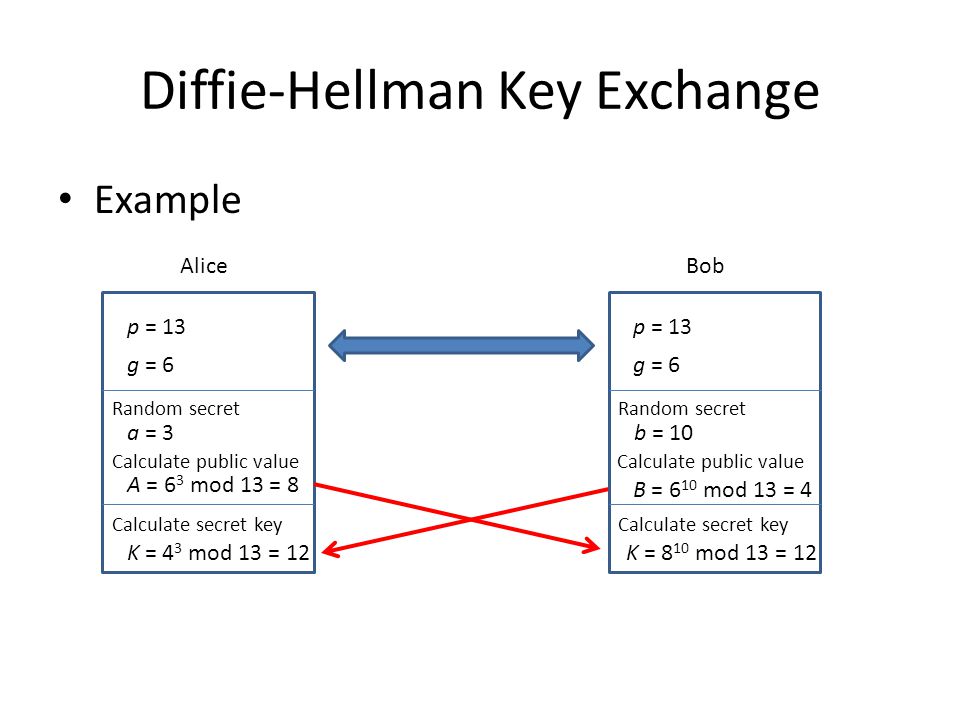
Security Keys Digital Signatures And Certificates I Ppt Download

Diffie Hellman Example Youtube

What Is The Diffie Hellman Key Exchange And How Does It Work
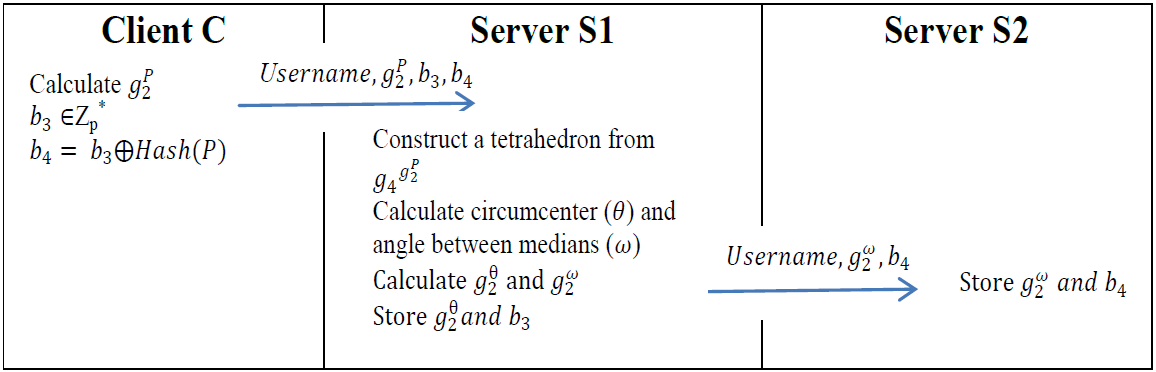
An Efficient 3d Diffie Hellman Based Two Server Password Only Authenticated Key Exchange

Imperfect Forward Secrecy How Diffie Hellman Fails In Practice January 2019 Communications Of The Acm

A Mathematical Explanation Of The Diffie Hellman Key Exchange Protocol The Sec Master
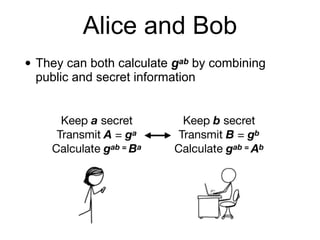
11 Diffie Hellman
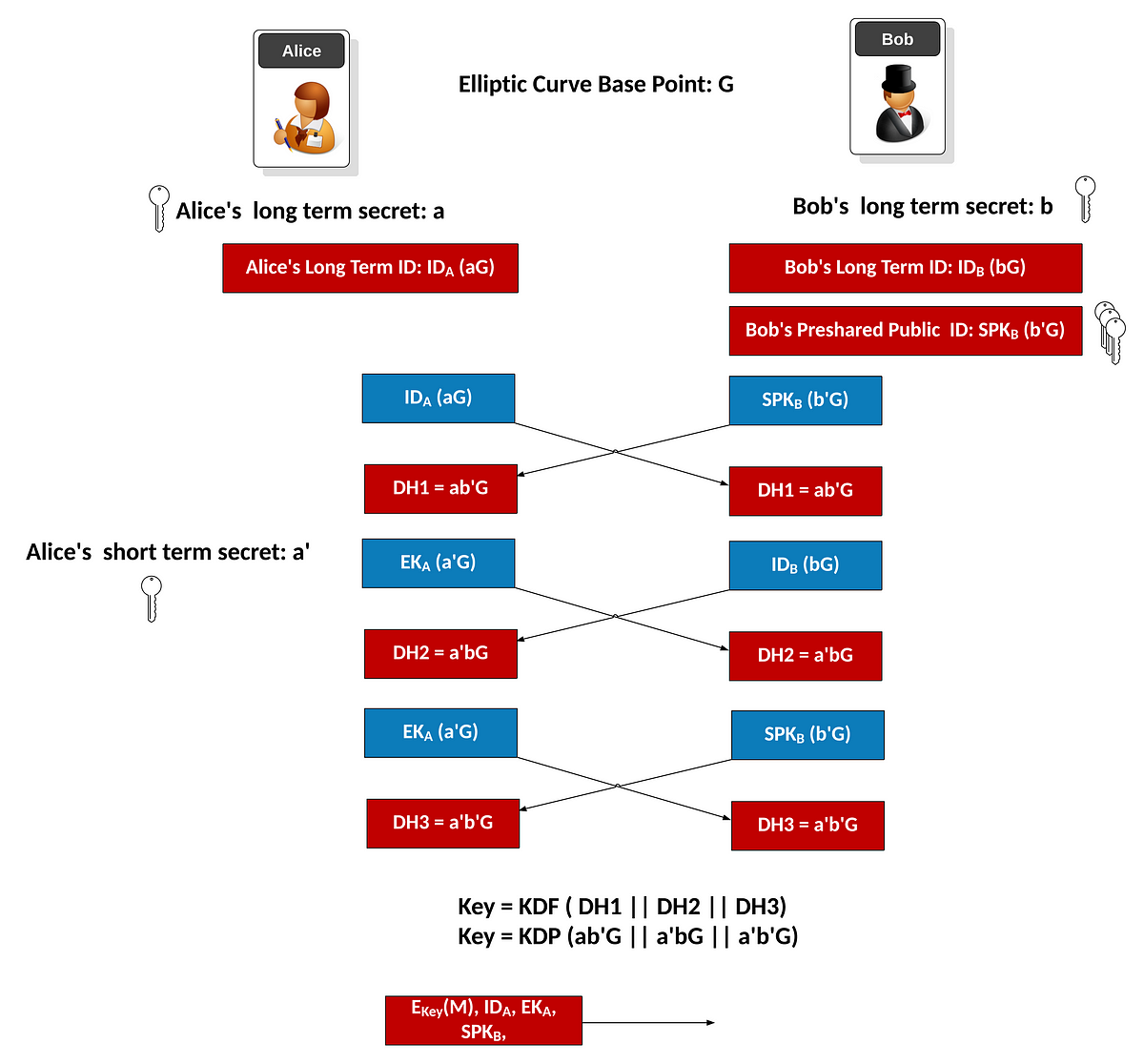
Alice Whispers To Bob At The Core Of Privacy In The 21st Century Is Extended Triple Diffie Hellman And Ratchets By Prof Bill Buchanan Obe Asecuritysite When Bob Met Alice Medium
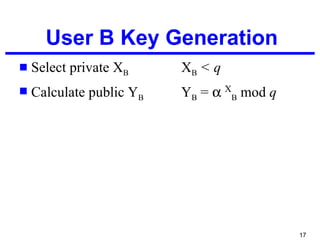
Diffiehellman

What Is The Diffie Hellman Key Exchange Just Cryptography